[ACTF新生赛2020]easyre
有UPX壳, 先脱壳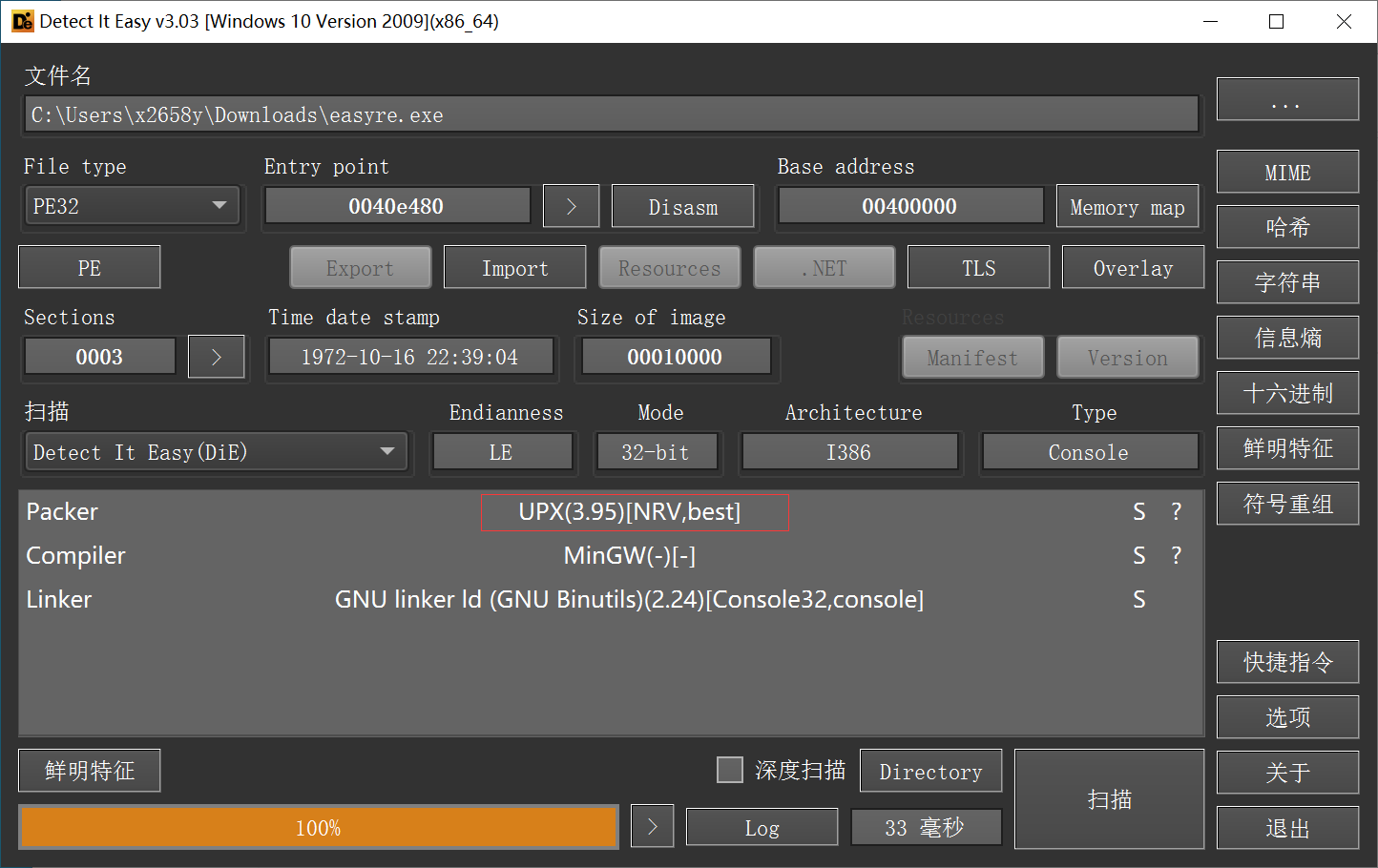
这次采用堆栈平衡法(esp定律法)来寻找popad,
从而找到程序的真正的入口. 也可以采用直接找popad的方法,
UPX一般可以这么干, 见 [BUUCTF]新年快乐
程序的入口点是一个pushad, F8让它执行,
改变esp, 对esp下硬件断点
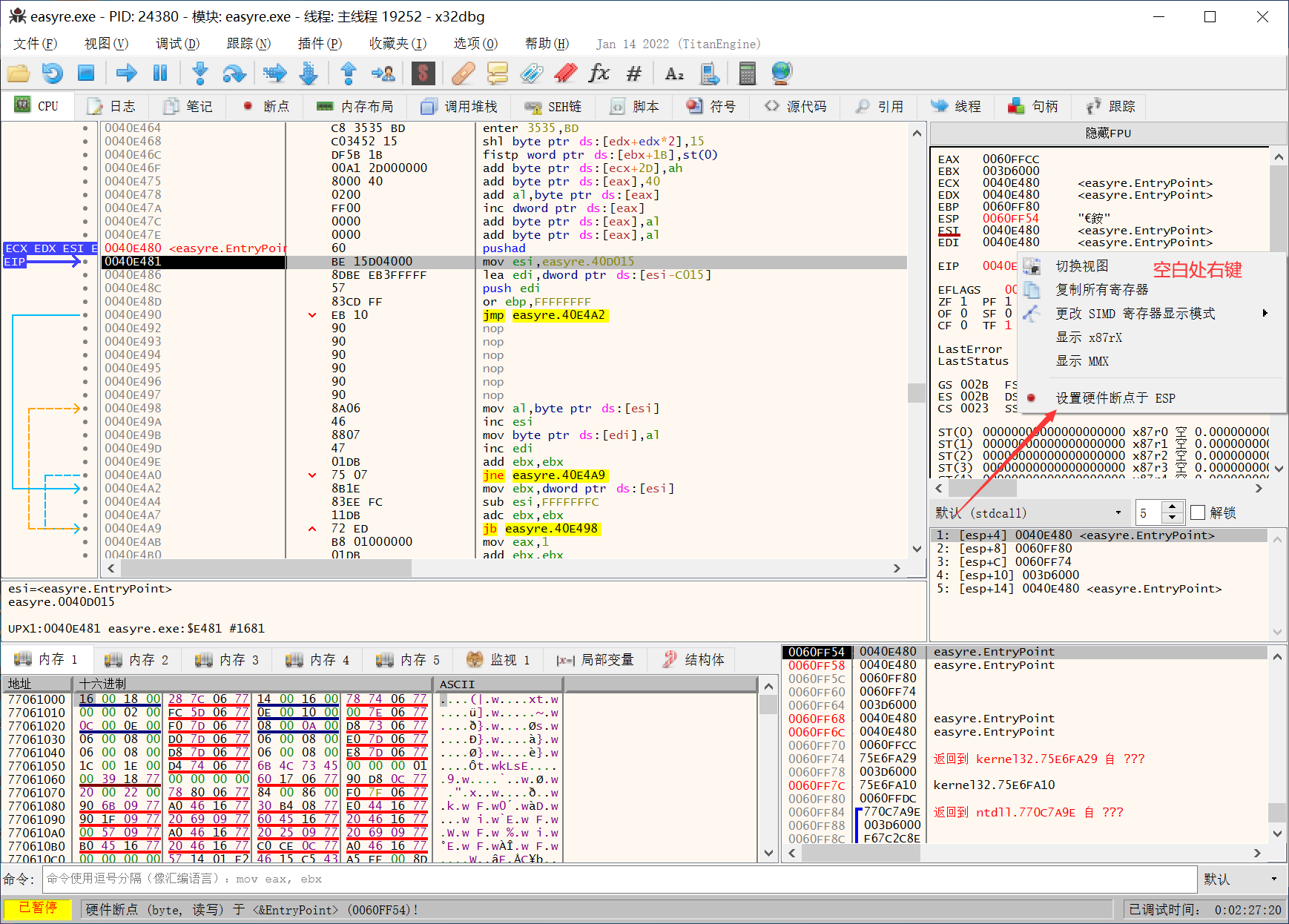
然后让程序跑起来, 被硬件断点断下,
可以看到刚好断在popad之后.
一般对于UPX来说popad之后的第一个jmp就是跳到程序真正的入口点,
这里是0x401280
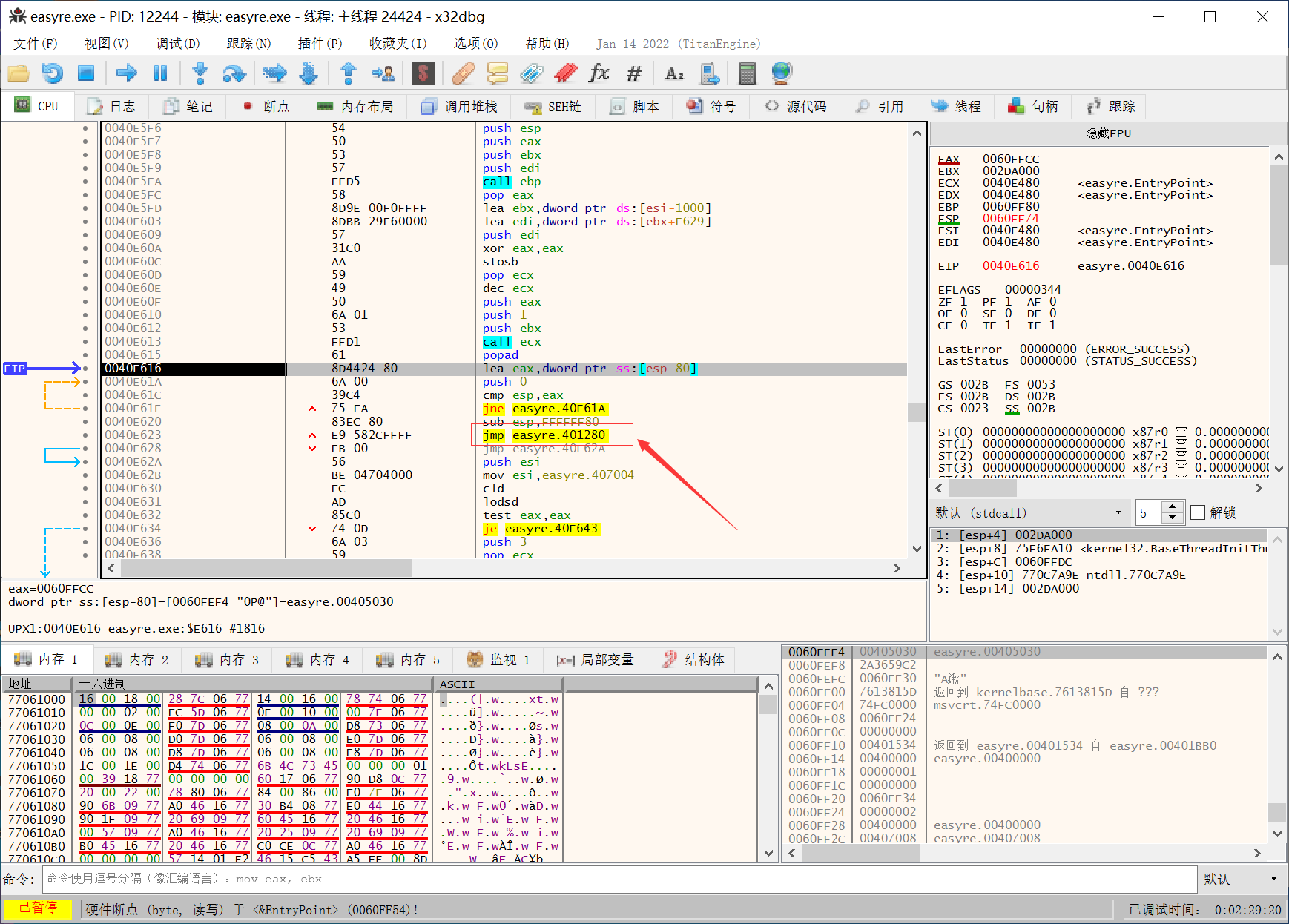
然后用Scylla插件脱壳, 用法见 [BUUCTF]新年快乐
脱壳完了拖进IDA, F5查看伪代码
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
取得v5的代码如下
1 |
|
我们就得出ACTF{U9X_1S_W6@T?}, 验证一下
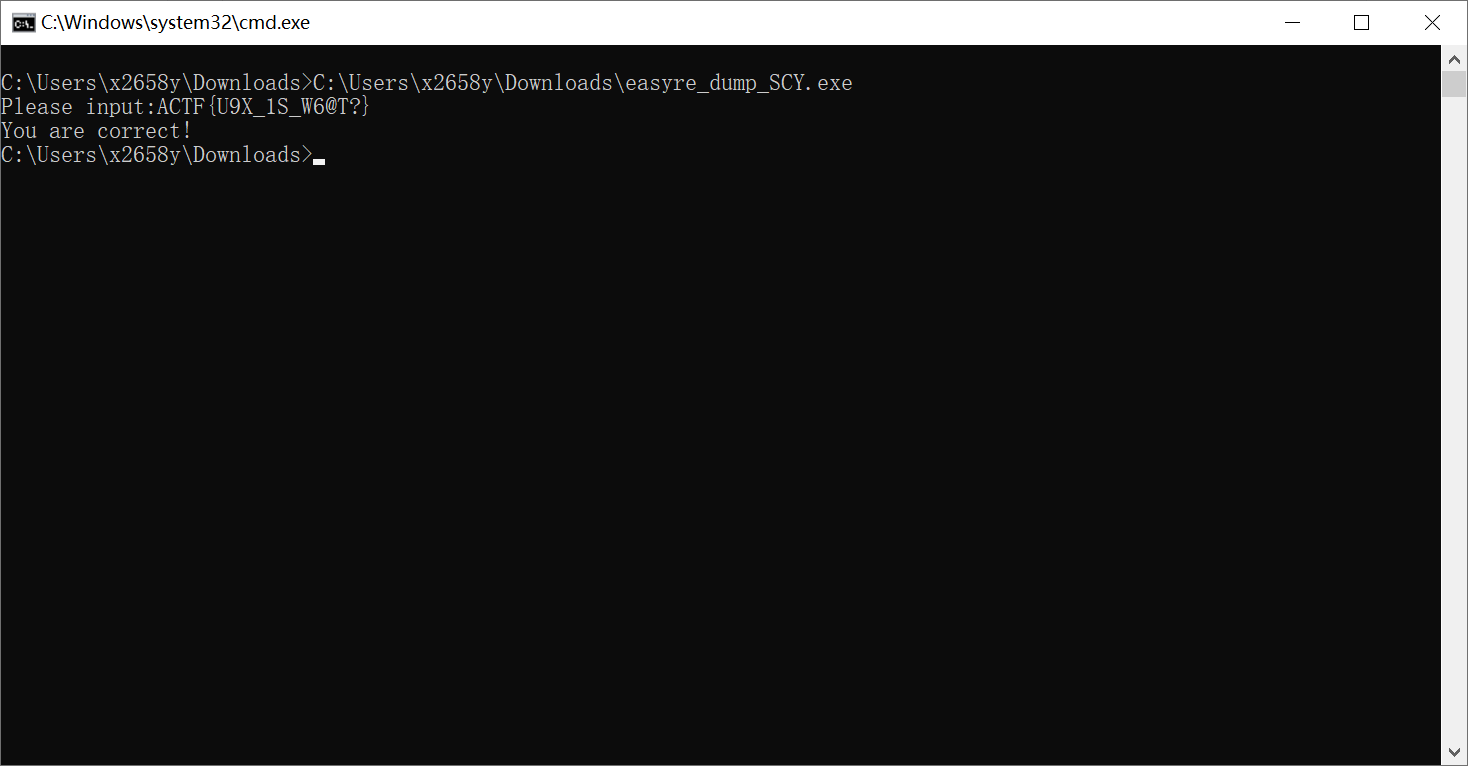
没问题,
所以flag就是flag{U9X_1S_W6@T?}