[2019红帽杯]easyRE
Linux可执行文件, 直接拖进IDA, F5查看伪代码,
但是有些复杂抓不住关键, 打开String窗口改由字符串入手.
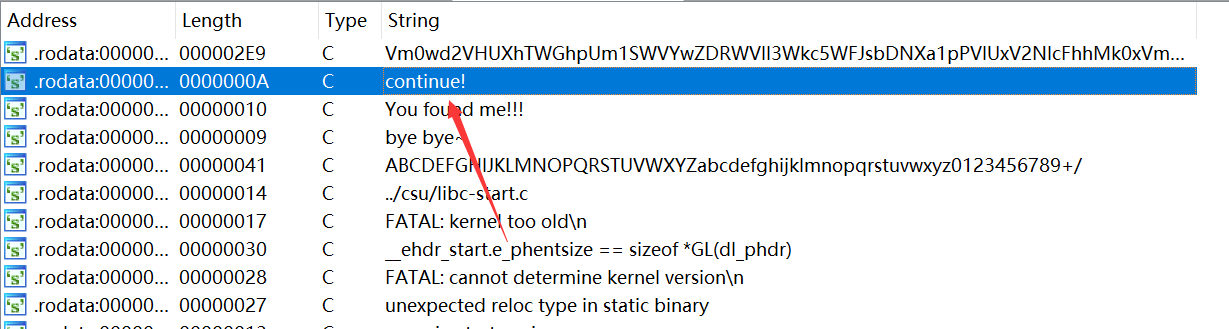
跟到字符串所在位置, 交叉引用确定程序语句再F5看伪代码, 直接找到关键点
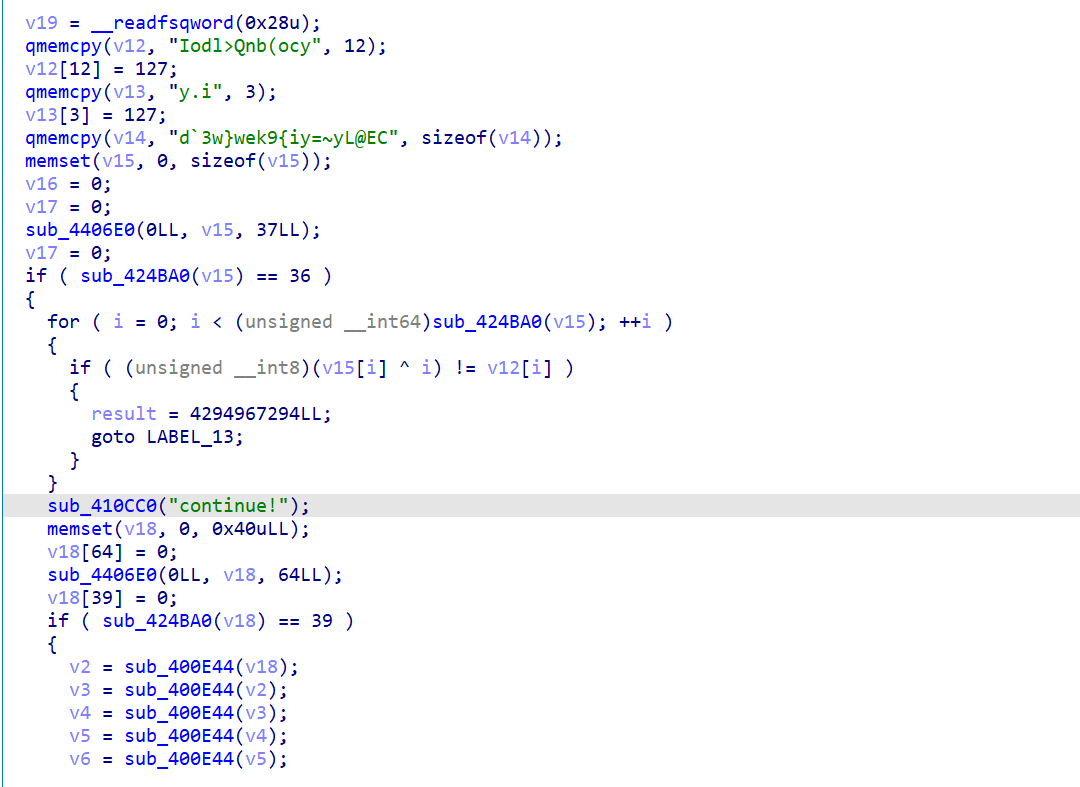
分析程序
1 | __int64 sub_4009C6() |
得到v15
1 | string = "Iodl>Qnb(ocy\x7fy.i\x7fd`3w}wek9{iy=~yL@EC" |
得到v18
1 | import base64 |
打开网站, 很好, 上当了...
看了别人的WP才知道答案原来从我眼前溜过了
off_6CC090这个字符串附近有点东西
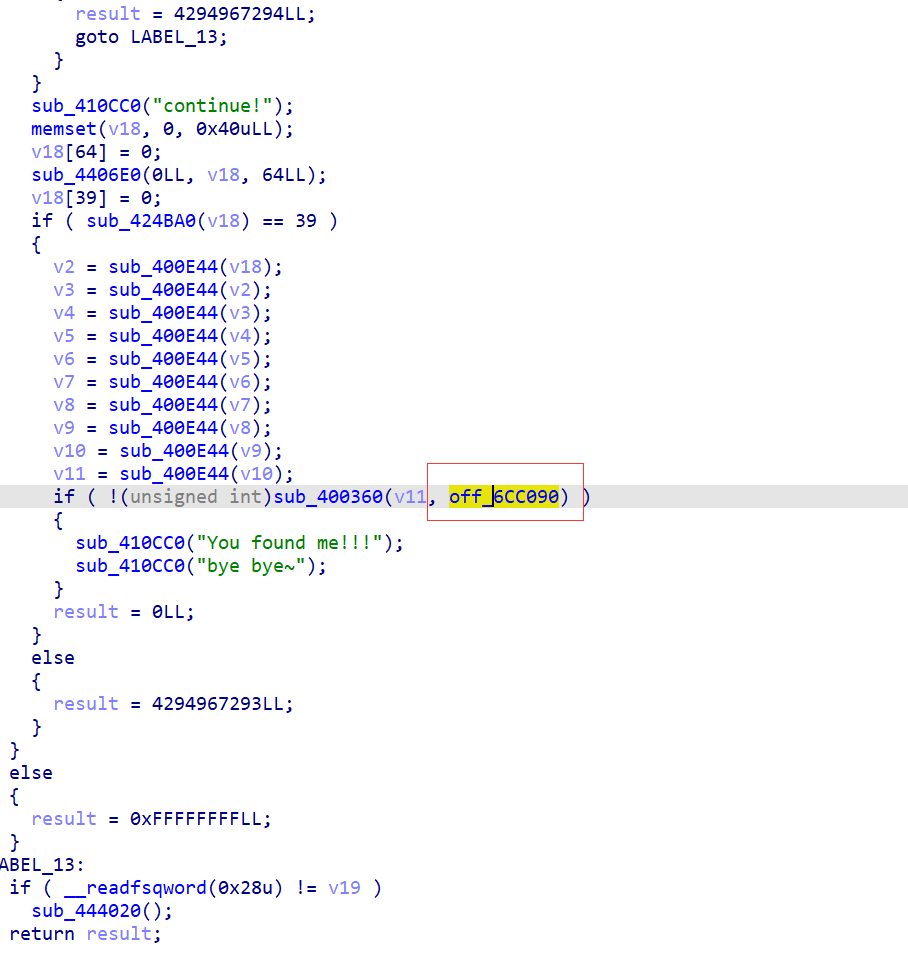
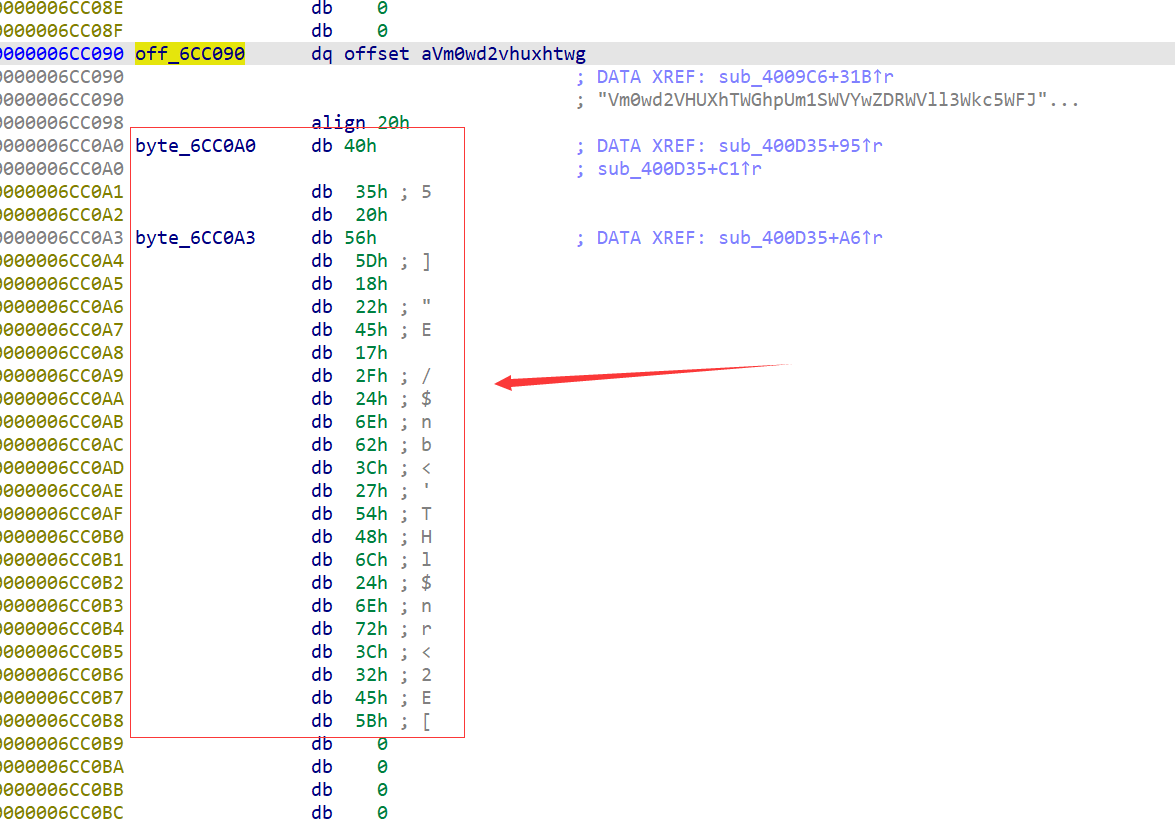
交叉引用找过去
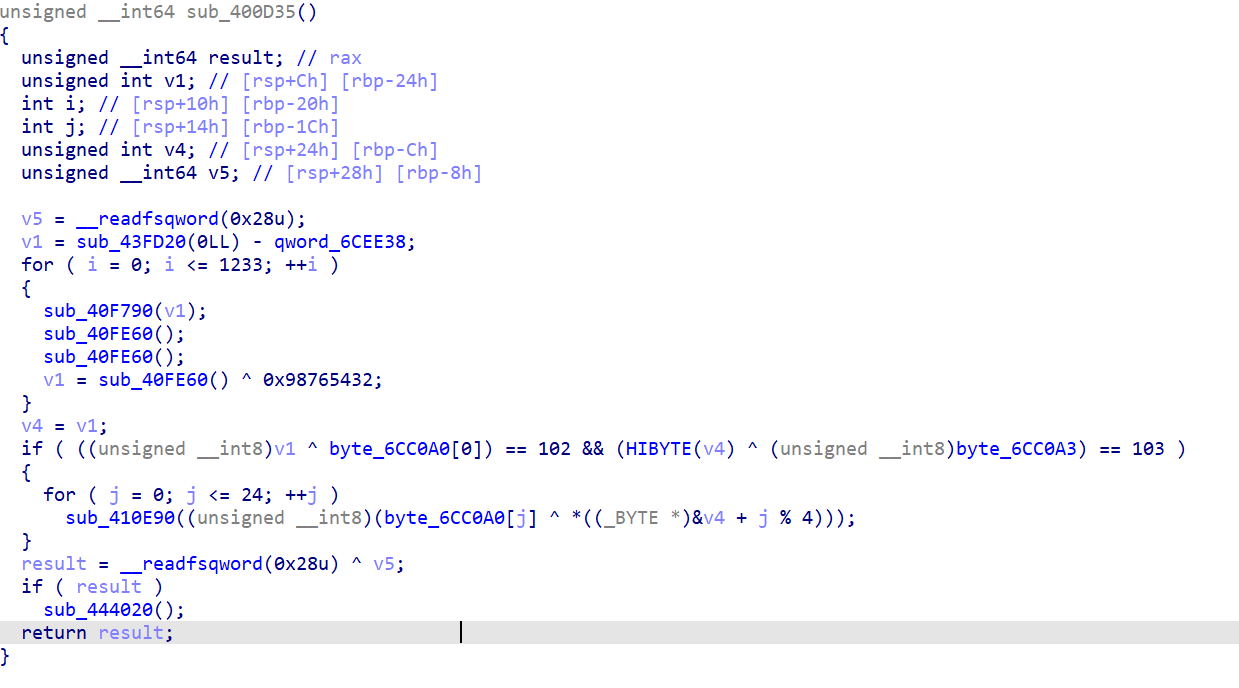
分析一下
1 | unsigned __int64 sub_400D35() |
解密代码如下
1 |
|