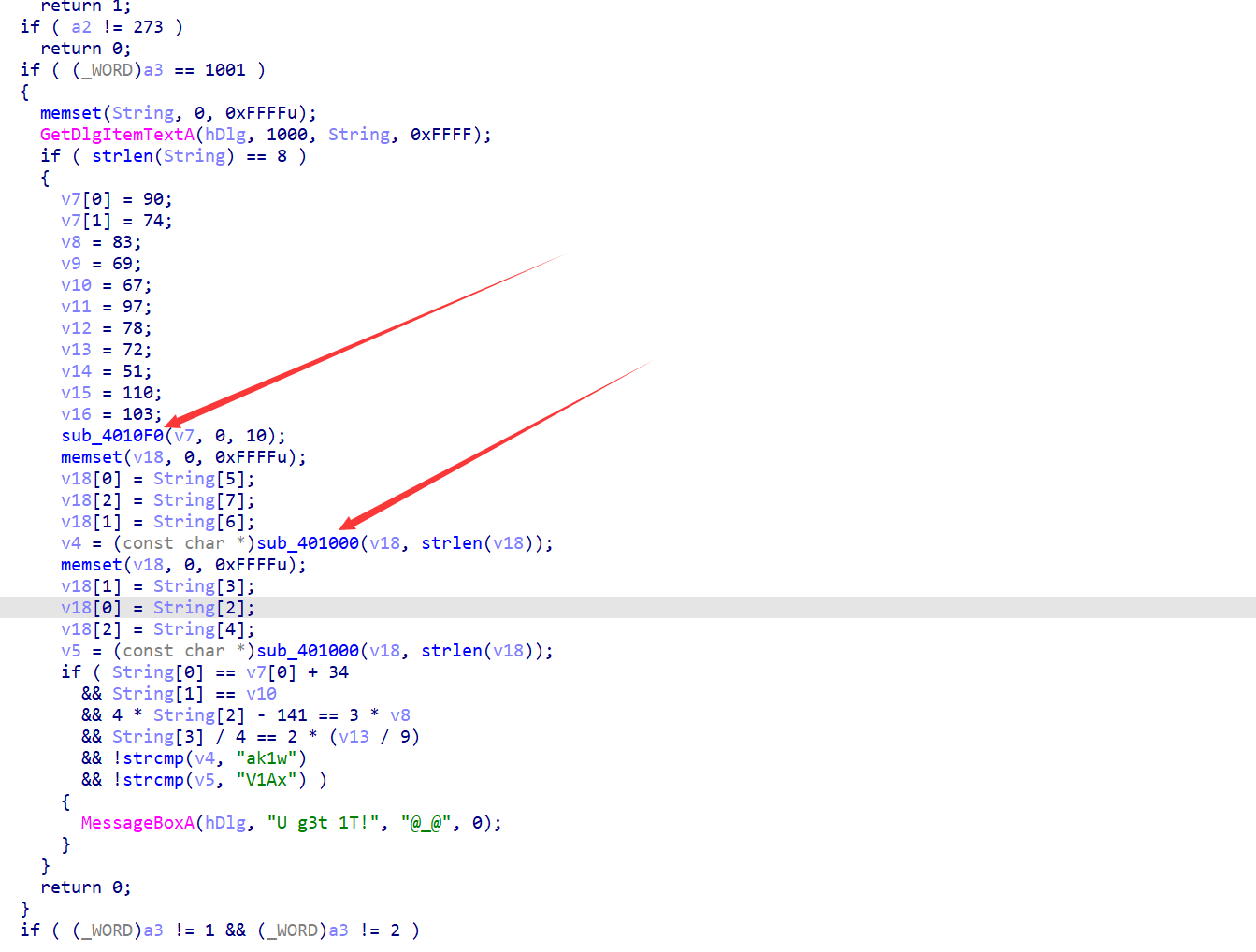
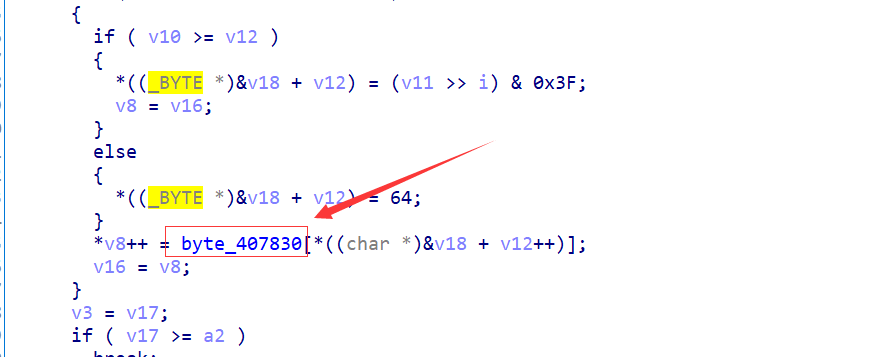
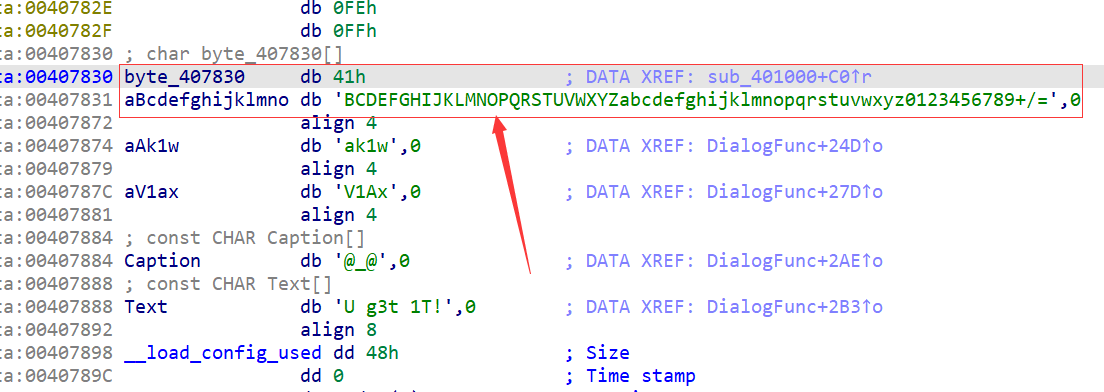
给的是一个Java字节码文件,
Java字节码的反编译还是比较容易的, 可以直接拿到源码,
采用jad反编译
jad反编译工具: 官网
Java源码如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
import java.io.PrintStream;
import java.util.ArrayList;
import java.util.Scanner;
public class Reverse
{
public Reverse()
{
}
public static void main(String args[])
{
Scanner s = new Scanner(System.in);
System.out.println("Please input the flag \uFF1A");
String str = s.next();
System.out.println("Your input is \uFF1A");
System.out.println(str);
char stringArr[] = str.toCharArray();
Encrypt(stringArr);
}
public static void Encrypt(char arr[])
{
ArrayList Resultlist = new ArrayList();
for(int i = 0; i < arr.length; i++)
{
int result = arr[i] + 64 ^ 0x20;
Resultlist.add(Integer.valueOf(result));
}
int KEY[] = {
180, 136, 137, 147, 191, 137, 147, 191, 148, 136,
133, 191, 134, 140, 129, 135, 191, 65
};
ArrayList KEYList = new ArrayList();
for(int j = 0; j < KEY.length; j++)
KEYList.add(Integer.valueOf(KEY[j]));
System.out.println("Result:");
if(Resultlist.equals(KEYList))
System.out.println("Congratulations\uFF01");
else
System.err.println("Error\uFF01");
}
}
|
没学过Java, 网上查了查不懂的地方,
这个程序的进行的操作如下:
把输入的字符串转成一个char数组,
char数组的每个元素加上64再与0x20异或,
再转成Integer类型放进列表Resultlist,
把KEY数组的每个元素也逐个转成Integer类型添加到另一个列表KEYList,
逐个元素比较判断Resultlist和KEYList是否相等
这里再次用到了关于异或的知识点, 见[BUUCTF]xor
解密代码如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| #include <cstdio>
using namespace std;
int main()
{
char str[] = {
180, 136, 137, 147, 191, 137, 147, 191, 148,
136,133, 191, 134, 140, 129, 135, 191, 65
};
for (int i = 0; i < sizeof(str); i++)
{
str[i] ^= 0x20;
str[i] -= 64;
putchar(str[i]);
}
}
|
所以flag就是flag{This_is_the_flag_!}